Hi folks!!!
Welcome to AWS Logging and Analysis quest...
In this article, we will be going to discuss about AWS Config service and how it can be utilized to monitor/oversee AWS Resources using a set of rules for configuration/compliance management.
Everything available in AWS is in the form of resource with an abstraction of service to do something with it. A resource is an entity with which we can work within AWS environment. For example, an EC2 instance is a resource which we can utilize to deploy our applications. Another example, is an S3 bucket which we can utilize for storing unstructured data/files. Every AWS resource is provided with a unique name called, Amazon Resource Name(ARN). I have launched an EC2 instance as App Server. We can observe in the CloudTrail event that the user who has created the instance is also identified by an ARN ("arn": "arn:aws:iam::xxxxxxxxxxxx:user/user-sysadmin1 ).
Collective management of AWS resources is necessary for governance, security analysis and configuration management. AWS Config helps in achieving the same. AWS Config works around a set of rules customizable and continuously monitor the resources to check for any violation. These rules are known as AWS Config Rules. In case of any violation to this rule, AWS config flags the resource as non compliant and we can configure SNS topic to get notified for the same.
Here, we will explore how AWS Config monitors for configuration changes for an EC2 instance creation and S3 bucket policy changes.
Scenario: Following are the compliance policies to be validated.
1. If an EC2 instance is launched with "instanceType" other than "t2.micro" i.e. free-tier eligible, mark it as non compliant otherwise compliant.
2. If an EC2 instance is launched in a VPC network other than specified one, i.e. "vpcId" is different, mark it as non compliant otherwise compliant.
3. If an S3 bucket is given read/write privilege mark it as non compliant otherwise compliant.
Steps to set the compliance:
Part 1 - Setting AWS Config
1. Go to Services --> Management Tools --> Config
2. If you are using AWS Config for the first time, select 'Get Started'. Otherwise, directly go to 'Settings'.
3. If 'Recording' is off, click 'turn on' to start the recording. Click 'Continue' in the pop up appeared.
4. Select 'S3: Bucket' and 'EC2: Instance' for the resource types to be recorded.
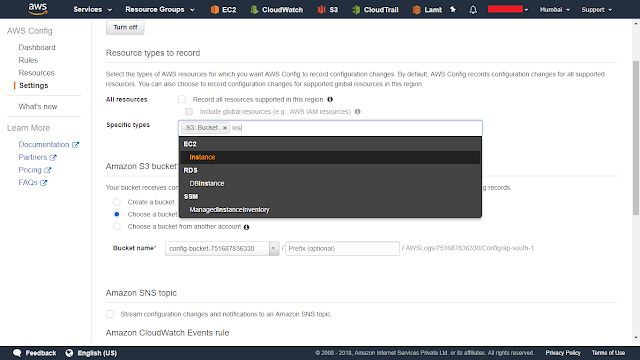 4. Select 'Create a bucket' option for storing configuration history for AWS Config records. Name the bucket in the space provided. e.g. 'config-compliance-ec2s3'
4. Select 'Create a bucket' option for storing configuration history for AWS Config records. Name the bucket in the space provided. e.g. 'config-compliance-ec2s3'
5. To stream configuration changes, check mark Amazon SNS topic. I have created one SNS topic with an email (Security_Team<Security_Team@company.com>) to notify security team for compliance failure/configuration changes.
6. Now, AWS Config will create a role on our behalf. This role will be given policies in IAM, keeping in mind two things:
a) The Config rule should be able to get all the read only events ( AWS Managed Policy - AWSConfigRole )
b) The Config rule should be able to push SNS to security team and config changes to S3. ( Managed Policy)
7. Hit 'Save' and then a message for success will appear.
Part 2 - Setting AWS Config Rule
1. Go to 'Rules' in AWS Config Console and select 'Add Rule'.
2. Type 's3' to search for S3 related rules. Select 's3-bucket-public-read-prohibited'.
3. Fill in appropriate 'Name', 'Description', 'Managed rule name'. Select 'Scope of changes' as 'Resources'. And in the 'Resources' fill 'S3: Bucket'.
4. Hit Save. Similarly, create a rule selecting 's3-bucket-public-write-prohibited'.
5. For EC2 compliance setup, fill in ec2 and select 'desired-instance-type'. Following the same, fill in appropriate 'Name', 'Description', 'Managed rule name'. Put 'instanceType' as t2.micro.
6. Following the same, set another rule for 'ec2-instances-in-vpc' providing the necessary vpc-id.
In the AWS Config Dashboard, observe the compliance state for the resources monitored.
It shows that one rule is non compliant i.e. 'ec2-instances-with-vpc'. I have one ec2 instance which is non compliant with this rule. Also the SNS event, received is revealing the same thing.
What if I terminate this instance, Will the Dashboard change?
Yes, the dashboard will monitor only S3 buckets and there will be no EC2 instances to monitor.
This is how AWS Config works to figure out the compliant and non compliant resources. AWS Config has its own limitation like it can only reveal the compliance nature of an AWS resource. Although its advantageous, as we can configure customize rules also but at the end, the admin/security team has to take specific action based on the compliance result. What if the action based on the compliance result can also be automated. We will look into the same in the next article.
Steps to set the compliance:
Part 1 - Setting AWS Config
1. Go to Services --> Management Tools --> Config
2. If you are using AWS Config for the first time, select 'Get Started'. Otherwise, directly go to 'Settings'.
3. If 'Recording' is off, click 'turn on' to start the recording. Click 'Continue' in the pop up appeared.
4. Select 'S3: Bucket' and 'EC2: Instance' for the resource types to be recorded.
 4. Select 'Create a bucket' option for storing configuration history for AWS Config records. Name the bucket in the space provided. e.g. 'config-compliance-ec2s3'
4. Select 'Create a bucket' option for storing configuration history for AWS Config records. Name the bucket in the space provided. e.g. 'config-compliance-ec2s3'5. To stream configuration changes, check mark Amazon SNS topic. I have created one SNS topic with an email (Security_Team<Security_Team@company.com>) to notify security team for compliance failure/configuration changes.
6. Now, AWS Config will create a role on our behalf. This role will be given policies in IAM, keeping in mind two things:
a) The Config rule should be able to get all the read only events ( AWS Managed Policy - AWSConfigRole )
b) The Config rule should be able to push SNS to security team and config changes to S3. ( Managed Policy)
7. Hit 'Save' and then a message for success will appear.
Part 2 - Setting AWS Config Rule
1. Go to 'Rules' in AWS Config Console and select 'Add Rule'.
2. Type 's3' to search for S3 related rules. Select 's3-bucket-public-read-prohibited'.
3. Fill in appropriate 'Name', 'Description', 'Managed rule name'. Select 'Scope of changes' as 'Resources'. And in the 'Resources' fill 'S3: Bucket'.
4. Hit Save. Similarly, create a rule selecting 's3-bucket-public-write-prohibited'.
5. For EC2 compliance setup, fill in ec2 and select 'desired-instance-type'. Following the same, fill in appropriate 'Name', 'Description', 'Managed rule name'. Put 'instanceType' as t2.micro.
6. Following the same, set another rule for 'ec2-instances-in-vpc' providing the necessary vpc-id.
In the AWS Config Dashboard, observe the compliance state for the resources monitored.
It shows that one rule is non compliant i.e. 'ec2-instances-with-vpc'. I have one ec2 instance which is non compliant with this rule. Also the SNS event, received is revealing the same thing.
What if I terminate this instance, Will the Dashboard change?
Yes, the dashboard will monitor only S3 buckets and there will be no EC2 instances to monitor.
This is how AWS Config works to figure out the compliant and non compliant resources. AWS Config has its own limitation like it can only reveal the compliance nature of an AWS resource. Although its advantageous, as we can configure customize rules also but at the end, the admin/security team has to take specific action based on the compliance result. What if the action based on the compliance result can also be automated. We will look into the same in the next article.

















0 comments: